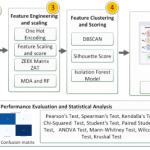
The scathing report concludes that Microsoft’s security culture needs an overhaul.
A new report from the US Cyber Safety Review Board has found that Microsoft could have prevented Chinese hackers from breaching US government emails through its Microsoft Exchange Online software last year. The incident, described as a “cascade of security failures” at Microsoft, allowed Chinese state-sponsored hackers to access online email inboxes of 22 organizations, affecting more than 500 people including US government employees working on national security.
The US Department of Homeland Security (DHS) has released a scathing report that found that the hack was “preventable” and that a number of decisions inside Microsoft contributed to “a corporate culture that deprioritized enterprise security investments and rigorous risk management.”
The hackers used an acquired Microsoft account (MSA) consumer key to forge tokens to access Outlook on the web (OWA) and Outlook.com. The report makes it clear that Microsoft still isn’t sure exactly how the key was stolen, but the leading theory is that the key was part of a crash dump. Microsoft published that theory in September, and recently updated its blog post to admit “we have not found a crash dump containing the impacted key material.”
Without access to that crash dump, Microsoft can’t be sure exactly how the key was stolen. “Our leading hypothesis remains that operational errors resulted in key material leaving the secure token signing environment that was subsequently accessed in a debugging environment via a compromised engineering account,” says Microsoft in its updated blog post.
:format(webp)/cdn.vox-cdn.com/uploads/chorus_asset/file/25368855/image.png)
Microsoft acknowledged to the Cyber Safety Review Board in November that its September blog post was inaccurate, but it was only corrected months later on March 12th “after the Board’s repeated questioning about Microsoft’s plans to issue a correction.” While Microsoft fully cooperated with the board’s investigation, the conclusion is that Microsoft’s security culture needs an overhaul.
“The Board finds that this intrusion was preventable and should never have occurred,” says the Cyber Safety Review Board. “The Board also concludes that Microsoft’s security culture was inadequate and requires an overhaul, particularly in light of the company’s centrality in the technology ecosystem and the level of trust customers place in the company to protect their data and operations.”
The findings from the board come in the same week that Microsoft has launched its Copilot for Security, an AI-powered chatbot designed for cybersecurity professionals. Microsoft is charging businesses $4 per hour of usage as part of a consumption model to access this latest AI tool, just as the company struggles with an ongoing attack from Russian state-sponsored hackers.
Nobelium, the same group behind the SolarWinds attack, managed to spy on some Microsoft executive email inboxes for months. That initial intrusion also led to some of Microsoft’s source code being stolen, with Microsoft admitting recently that the group accessed the company’s source code repositories and internal systems.
Microsoft is now attempting to overhaul its software security following the breach of US government emails last year and similar cybersecurity attacks in recent years. Microsoft’s new Secure Future Initiative (SFI) is designed to overhaul how it designs, builds, tests, and operates its software and services. It’s the biggest change to Microsoft’s security efforts since the company introduced its Security Development Lifecycle (SDL) in 2004 after the devastating Blaster worm that hit Windows XP machines offline in 2003.
This post was originally published on the 3rd party site mentioned in the title of this this site