Governance & Risk Management
,
Managed Detection & Response (MDR)
,
Network Detection & Response
Gartner’s Thomas Lintemuth Shares Insights on Modern Network Security Strategies
At the Security and Risk Management Summit in Mumbai, India, earlier this year, Thomas Lintemuth, vice president analyst at Gartner, presented an overview of how network security tooling has evolved. He discussed the current landscape, which includes a combination of traditional technologies including firewalls and modern technologies such as secure service edge – SSE, network detection and response – NDR, and secure access service edge – SASE.
See Also: Shift From Perimeter-Based to Identity-Based Security
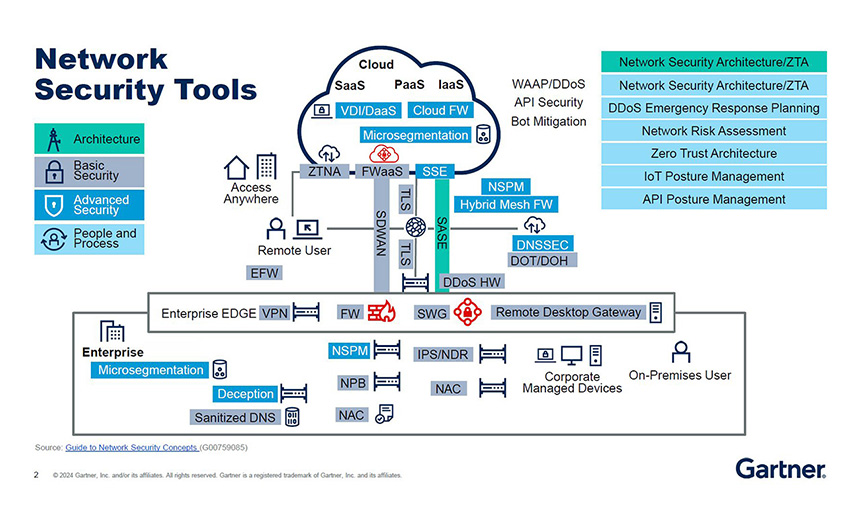
Lintemuth explored traditional and new network security technologies and frameworks, but pointed out that while some experts have dismissed older technologies such as VPN and network firewalls, they remain relevant in a zero trust environment, though in new forms (see: Image 1).
“Technologies like network firewall and network access control continue to be relevant and play their part in the outlook for network security,” Lintemuth said. “But there are also new technologies like deception and network detection and response that play into zero trust.”
No organization has complete visibility into their network, he said, and NDR adds value by establishing a baseline for normal activity and alerting “us when something unusual or mischievous is happening on the network.”
Network Security Challenges
In addition to persistent threats such as API and DDoS attacks targeting networks, other challenges in adopting security tools and frameworks include:
- Pricing models: The absence of transparency in pricing models, with vendors charging by appliance, per user, per device monitored or per throughput, has resulted in confusion among buyers who consume services.
- Hybrid workloads and workers: Most organizations have adopted a hybrid working model during and after the COVID pandemic, with only 4% not supporting it, according to a Gartner survey. The need to migrate workloads to multiple clouds and re-architecture networks to support remote workers added complexity.
- Wireless networks: While Wi-Fi remains the most popular wireless connectivity option for workers, Gartner predicts that by 2025, 60% of enterprises will have five or more wireless technologies bridged across an intelligent connectivity overlay, up from less than 3%. A Gartner report says that 50% of enterprise wireless endpoints will use networking services that deliver additional capabilities beyond communication, up from less than 15% in 2022.
- Other challenges: As more automation is introduced in network security, network engineers must re-configure networks accordingly. With an increasing number of IoT and OT devices connecting to the IT network, additional security challenges may arise as these devices are notoriously less secure. Enterprises also must address the skills gap in recruitment and hiring.
Secure What You Do Not Own
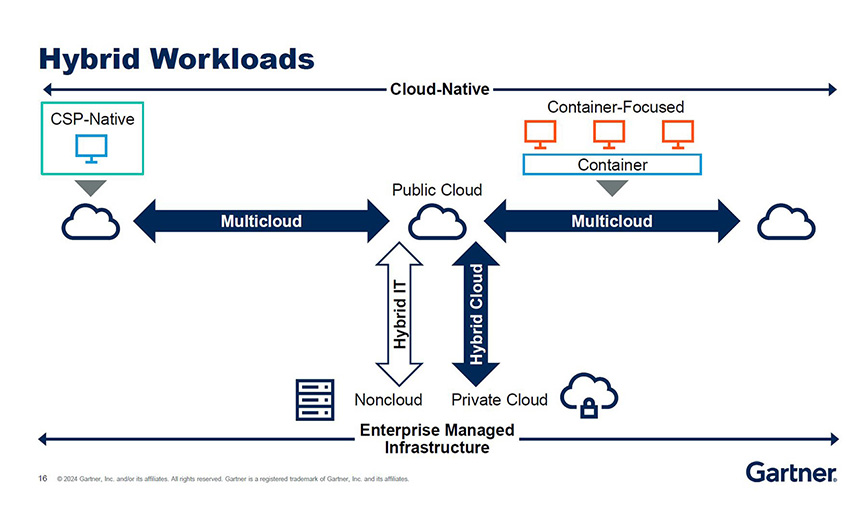
As organizations increasingly move their applications and security controls to the cloud, control shifts to hyperscalers that own and rent out the cloud resource on a pay-per-use basis. Securing this infrastructure becomes a shared responsibility between the cloud service provider and the organization using the services. With data spread across multiple clouds, data security and data residency are major concerns.
“After speaking to Gartner clients, I found that 60% have three or more cloud service providers,” Lintemuth said. “What if you’re using an AWS security control and you also have workloads in Azure? That means I now have to use the security controls of Azure as well, and I may still have to use my security controls on premises.”
This scenario requires training in-house engineers on security tools for multiple cloud environments, which can be challenging in the current skills shortage (see: Image 2).
“While it is better to have multiple clouds, it makes a lot of sense to find one vendor or third party who can manage the entire security and have a single point of control, a single point of reporting and a single point of compliance,” Lintemuth said.
Secure an Expanding Footprint
Network infrastructure has an expanding footprint as workloads and infrastructure move from on-premises to multiple clouds. Hardware-based security appliances are being replaced by software agents in the scenario where they are not compatible with a particular cloud. These agents, which are deployed on workloads, are “a leading way to do microsegmentation” and can also be put on workloads to act as “enforcement points” for policies, Lintemuth said. He advised leveraging multiple enforcement points for network security – hardware, software, services and agents – across on-premises, hybrid and cloud environments.
Lintemuth advised against over-deployment of microsegmentation. “If you try to control 10,000 servers with microsegmentation, you’re probably going to drive yourself crazy because of all the operational complexity that you’re introducing,” he said. “When you’re doing microsegmentation, you want to start with your key assets. Once you have your key assets secured, then you can figure out how much further you need to expand the project. But it would be incredibly rare that you would want to do enforcement across your entire estate,” he said.
Cloud firewalls – offered by vendors as virtual, cloud-native and containerized firewall services – are another way to secure the expanding footprint.
Users and Endpoints
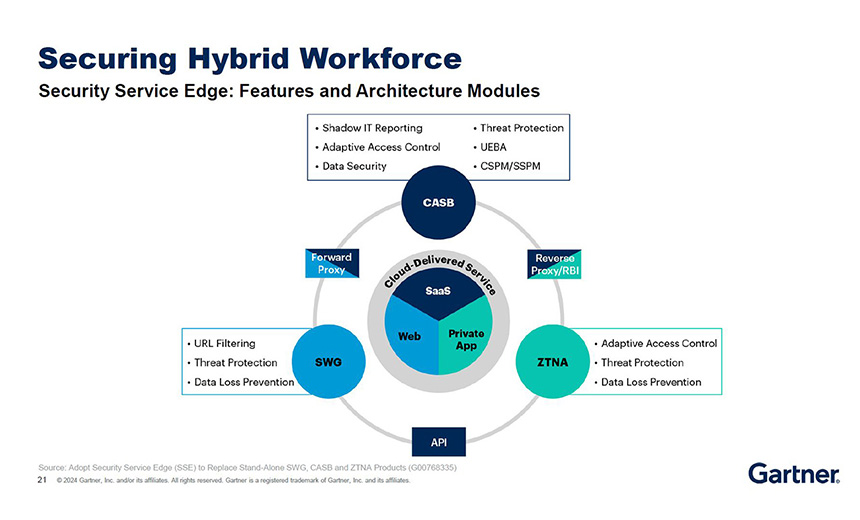
Despite implementing the best security solutions, human errors often compromise network security. Corporate endpoints are secured with EDR solutions, but problems occur when users connect unsecured personal devices to the network. When security controls deny access to certain resources, users try to find workarounds such as using their personal hot spots for connectivity or using browser extensions instead of installing applications, which poses a significant risk, especially if corporate data is present on unsecured devices.
“Security service edge is the uniting of ZTNA, CASB and SWG, and it puts an enforcement point between users and the applications they’re trying to access,” Lintemuth said. “What’s more, the application can be hosted anywhere and it can be a sanctioned or unsanctioned SaaS application. The agent directs all the traffic to an enforcement point, which is SSE on the cloud.”
Lintemuth said SSE is an essential technology since it can manage access to applications from unmanaged devices (see: Image 3).
Focus, Embrace and Improve
To navigate this security technology landscape, Lintemuth recommends security leaders follow these steps:
- Focus: Think about how you are going to use fabrics with technologies and services. The best vendors offer convergence around key problems to solve, but security professionals must prioritize open integration through open standards to improve the overall security posture of an organization.
- Embrace: Practitioners should adopt technologies and frameworks such as cybersecurity mesh architecture – CSMA – and extended detection and response – XDR – that bring signals from different vendors together.
- Improve: Enterprises must aim to address API threats and advanced DDoS attacks, evolve existing controls when possible, and continue upskilling employees.
This post was originally published on the 3rd party site mentioned in the title of this this site