Your web application’s front end is the first part seen everywhere. It’s the first thing that regular users and potential customers look at but it’s also the first thing that an attacker sees—it’s the main door to your attack surface.
Front-end security demands have increased a lot over the past decade. There are more sophisticated attacks taking place against web application front ends these days, whereas in the past most attacks were straightforward, resulting in easier detection. More recently, attacks have become stealthier, harder to detect, and often discovered far too late.
Employing proactive techniques, like engaging security from the start, reducing security by obscurity, and nurturing a healthy cybersecurity culture within an organization, can help reduce the attack surface of any web application’s front end.
Top 10 Front-End Security Risks and Best Practices to Prevent Them
Let’s look at some popular front-end security issues, and how you can fight different types of threat actors to prevent them with the industry’s best practices.
1. Preventing cross-site scripting (XSS) attacks
XSS attacks are one of the largest and most dangerous forms of attack. They’re crafted in such a way that they inject code into a web application, which ends up performing malicious actions when accessed by an end user.
XSS attacks are drawn to a lack of sanitization in a web application’s input and output, which can lead to a variety of attacks.
Clickjacking attacks
Clickjacking attacks rank as one of the largest types of attacks under the XSS attack umbrella, as they’re simply performed by replacing legitimate parts of a web page with similar-looking, yet dangerous, elements. For example, checkout buttons can be replaced with buttons redirecting users to fake banking pages, legitimate download buttons can be replaced with buttons resulting in malware downloads, and more.
Geolocation stealing
With XSS attacks, an attacker can inject JavaScript libraries, which then execute on the client side—logging the user’s IP address, geolocation and other personal details. These can then be used by the attacker to target the end user with personalized scams or phishing.
Cryptomining
With code injected by an XSS attack, cryptomining can be performed on end users’ devices as well. While it may already seem to slow down a single device, hundreds or thousands of users visiting a web application every day means crypto mining scripts running on your web application can unknowingly cause not only slowdowns but also heating issues on users’ devices. This sort of effect on your web application can lead to a negative experience on their part.
Protection against XSS attacks can be achieved by the proper sanitization of inputs made into your web application, as well as by filtering inputs correctly. For example, limiting mobile numbers to digits only or not allowing special characters in names can yield a substantial benefit by preventing most injection attacks on your web application.
2. DoS (denial of service) attacks
DoS attacks and DDoS attacks on web applications are common. They’re also difficult to deal with, as they use a swarm of compromised systems to make requests to your web application.
DoS attacks, which originate from a single system or small number of them, can often be tackled by simply blocking the end system’s IP address.
DDoS attacks, on the other hand, are more difficult to block. This is because certain DDoS attacks originate from hundreds or thousands of systems at the same time—meaning they also make multiple thousands or millions of requests to your web application simultaneously—leading to system strain and a serious slowdown of your web application.
Employing rate-limiting in your web application can prevent these types of attacks. Look to services like CloudFlare or Imperva, or hardware-based solutions; these can filter such attacks before they reach their intended target.
3. Preventing cross-site request forgery (CSRF)
CSRF attacks are aimed at tricking users into submitting forms which end up performing a different action from the one the user wishes to perform.
For example, a user is logged into his banking application and browsing the internet at the same time. The user then comes across a “Download” button which he clicks on, and instead of actually downloading anything for the user, that fateful click transfers funds from the user’s bank account to the attacker.
CSRF attacks can be prevented by using a token value similar to an md5sum or sha256sum of random characters, which is generated on every page load and passed to a form via HTTP headers, upon the submission of any form.
If the header token value is missing or if there is a token mismatch, the action is not performed and the user remains safe.
4. Using Content Security Policy (CSP)
Using Content Security Policy is an effective form of XSS attack prevention. It calls for an HTTP flag which informs your browser about the sources that can be trusted, and included as iFrames within your web application.
Any source or URL not mentioned within the Content Security Policy flag is discarded, and will not be included or rendered within an iFrame on your web application.
Enabling CSP in your HTTP headers is a worthwhile method of preventing XSS attacks to a large extent. And when combined with X-Frame-Options, it provides a solid defense against XSS attacks in general.
5. Using modern frameworks
Often, web application front ends are built using commonly available frameworks. These frameworks make up the core of your web application’s front end (cybercriminals already know this) and any security vulnerability within this framework can lead to a compromise of your web application as a whole.
Using modern and frequently updated frameworks can help boost your web application’s security. These frameworks frequently include built-in authentication handlers and other security features that help standardize the security practices needed for your web application.
6. Auditing of 3rd-party libraries in use
3rd-party libraries are in use everywhere. They help speed up coding time and make implementation of new features into your web application that much easier—but any possible vulnerability in these 3rd-party libraries can impact your web application’s overall security as well.
For example, many web applications rely on 3rd-party libraries for handling billing and customer purchases. Any vulnerability in these billing libraries can cause multiple security issues in your web application, such as the leaking of user information or redirecting users to phishing domains to capture card details.
Keeping track of and scanning 3rd-party libraries manually can often be tricky for large web applications, but online vulnerability scanners exist to help this process along, making it straightforward, automated, and ready to alert you whenever a vulnerability is found.
7. Incorporating security from the start
Web application development generally runs for months if not years. Developers come, developers go, budgets change, ideas change and projects change direction.
During all these changes, ensuring that your project stays secure is the most important aspect to consider to avoid any cybercrime event. Incorporating a security-first approach in your project from the very start ensures that your project will stay secure no matter what changes come along.
8. Avoiding iFrames where possible
While iFrames make your development process easier by allowing you to incorporate/load other pages/frames in your existing view, iFrames usage is often used without appropriate X-Frame-Options. Unfortunately, this allows for clickjacking attacks and the compromise of your web application’s integrity.
iFrame-based attacks can be used to play videos, open malicious forms (which look legitimate), and trick users into downloading malicious content that can lead to a degraded overall experience of your web application.
9. Restricting available Feature Policy
By default, your web application can access or request any feature from your end user’s device—while this may be a nice-to-have during the development stage, if left enabled it can lead to attackers exploiting your web application and using these unrestricted feature flags/policies to ask end users’ devices to enable certain features that appear legitimately offered by your web application itself.
Using the Feature-Policy HTTP header is ideal for preventing such requests from originating from your web application.
For example, setting the following Feature-Policy will alert the end users’ web browsers to not enable these features, even if requested by your web application:
"Feature-Policy": camera 'none'; microphone 'none';
10. Ensuring CDN-pulled libraries undergo subresource integrity checks
Also critical is checking whether libraries loaded via 3rd-party CDNs are intact and untouched.
Many web applications load libraries off 3rd-party CDNs for quicker loading of pages and better overall performance, but if these libraries are compromised via MITM attacks or if the CDN itself is compromised, it’s possible to load bad code into your web application on the user side, leading to a poor experience.
For example:
<link href="https://cdn.jsdelivr.net/npm/[email protected]/dist/css/bootstrap.min.css" rel="stylesheet" integrity="sha384-BmbxuPwQa2lc/FVzBcNJ7UAyJxM6wuqIj61tLrc4wSX0szH/Ev+nYRRuWlolflfl" crossorigin="anonymous">
The above code loads the popular Bootstrap CSS library but includes an integrity parameter with a checksum, which can be verified by your browser. This ensures that if the CDN is compromised and the CSS file is modified, the integrity checksum will not match and the file will not render in your user’s browser.
At the expense of a poorly rendered page (at most), this will help protect your web application’s reputation and security, while keeping your user safe as well.
Front-end security covers only a part of the surface
The security game doesn’t end when you finish hardening your front-end security checklist, it’s only the beginning. Your attack surface is a much larger area that must be analyzed and secured properly.
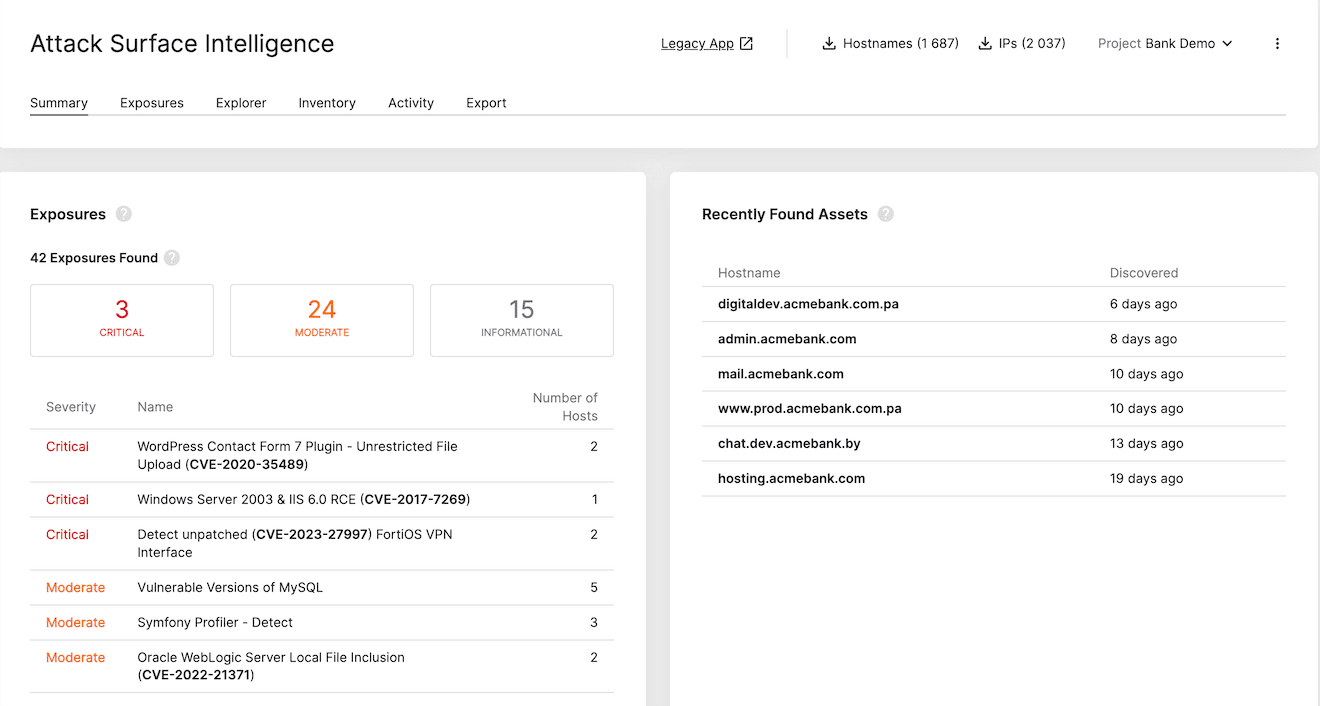
By using solutions like Recorded Future’s Attack Surface Intelligence, you’ll be able to analyze other aspects of your backend security, such as:
Conclusion
Securing your web application’s front end has become an increasingly important factor to consider. With applications facing multiple threats on a daily basis, dealing with everything from automated bots to targeted attacks, keeping your application’s front end safe has never been more crucial.
Hardening the front-end side of your web apps remains a challenge, but incorporating security from the start—and relying on modern web frameworks, content security policy, frequent auditing, scanning of 3rd-party libraries in use, as well as analyzing your attack surface—can greatly increase the chances of keeping your web application’s front end safe.
To further protect your expanding attack surface, explore the Recorded Future Attack Surface Intelligence module and book a demo today.
This post was originally published on the 3rd party site mentioned in the title of this this site