On March 27, 2024, the U.S. Cybersecurity and Infrastructure Security Agency’s (“CISA”) Notice of Proposed Rulemaking (“Proposed Rule”) related to the Cyber Incident Reporting for Critical Infrastructure Act of 2022 (“CIRCIA”) was released on the Federal Register website. The Proposed Rule, which will be formally published in the Federal Register on April 4, 2024, proposes draft regulations to implement the incident reporting requirements for critical infrastructure entities from CIRCIA, which President Biden signed into law in March 2022. CIRCIA established two cyber incident reporting requirements for covered critical infrastructure entities: a 24-hour requirement to report ransomware payments and a 72-hour requirement to report covered cyber incidents to CISA. While the overarching requirements and structure of the reporting process were established under the law, CIRCIA also directed CISA to issue the Proposed Rule within 24 months of the law’s enactment to provide further detail on the scope and implementation of these requirements. Under CIRCIA, the final rule must be published by September 2025.
The Proposed Rule addresses various elements of CIRCIA, which will be covered in a forthcoming Client Alert. This blog post focuses primarily on the proposed definitions of two pivotal terms that were left to further rulemaking under CIRCIA (Covered Entity and Covered Cyber Incident), which illustrate the broad scope of CIRCIA’s reporting requirements, as well as certain proposed exceptions to the reporting requirements. The Proposed Rule will be subject to a review and comment period for 60 days after publication in the Federal Register.
Covered Entities
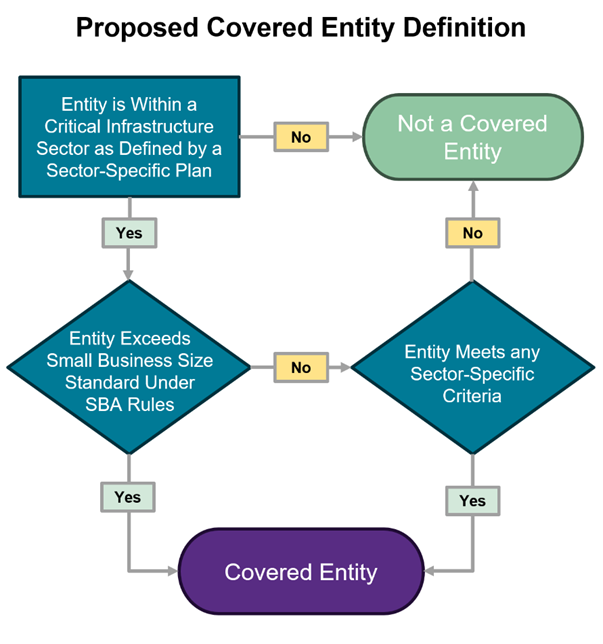
CIRCIA broadly defined “Covered Entity” to include entities that are in one of the 16 critical infrastructure sectors established under Presidential Policy Directive 21 (“PPD-21”) and directed CISA to develop a more comprehensive definition in subsequent rulemaking. Accordingly, the Proposed Rule (1) addresses how to determine whether an entity is “in” one of the 16 sectors and (2) proposed two additional criteria for the Covered Entity definition, either of which must be met in order for an entity to be covered. Notably, the Proposed Rule’s definition of Covered Entity would encompass the entire corporate entity, even if only a constituent part of its business or operations meets the criteria. Thus, Covered Cyber Incidents experienced by a Covered Entity would be reportable regardless of which part of the organization suffered the impact. In total, CISA estimates that over 300,000 entities would be covered by the Proposed Rule.
Decision tree that demonstrates the overarching elements of the Covered Entity definition. For illustrative purposes only.
16 Critical Infrastructure Sectors. Consistent with CIRCIA, the proposed regulatory text of the Covered Entity definition includes that entities must be “in a critical infrastructure sector,” but the text does not define this term or describe how to determine which entities are within those sectors. However, the commentary in the Proposed Rule states that this threshold question is effectively tied to the sector descriptions in the critical infrastructure Sector-Specific Plans (“SSPs”) that were developed pursuant to PPD-21. Thus, entities can rely on the SSPs to determine if they are “in” a sector. Notably, the scope of the SSPs is not limited to owners and operators of critical infrastructure systems and assets. Accordingly, the Proposed Rule indicates that reporting requirements would also apply to a “small subset” of entities covered in the SSPs that are “active participants” in a particular sector and that can impact the security of critical infrastructure.
Additional Criteria. The Proposed Rule then outlines two additional scoping criteria for the definition of Covered Entity: (1) the size of an entity and (2) whether the entity meets certain sector-based criteria. A critical infrastructure entity that falls within one of the 16 sectors described above need only fall within one of these categories to be a Covered Entity.
- Size-Based Criteria. Under the Proposed Rule, any entity within a critical infrastructure sector that exceeds the U.S. Small Business Administration’s (“SBA”) small business size standard as specified by the applicable North American Industry Classification System (“NAICS”) code would be a Covered Entity. These standards vary by industry and are generally based on an entity’s number of employees or annual revenue. Under the Proposed Rule, each entity would follow the SBA’s rules for calculating size and revenue, including identifying which NAICS code must be applied to determine whether it meets the size-based criteria. Depending on the industry, the SBA standard’s employee and revenue thresholds can vary significantly.
- Sector-Based Criteria. The Proposed Rule specifies that Covered Entities would also include any entity within a critical infrastructure sector that meets one or more enumerated sector-based criteria, regardless of whether it exceeds the above-referenced SBA standards. These criteria are generally based on whether entities own or operate certain facilities or perform key functions. High-level summaries of the sector-based criteria are provided in the table below.






The Proposed Rule does not include any separate sector-based criteria for the Commercial Facilities Sector, the Dams Sector, or the Food and Agriculture Sector, and would instead rely on the size-based or overlapping sector-based criteria to determine which entities in these sectors qualify as Covered Entities.
Covered Cyber Incidents and Ransomware Attacks
CIRCIA requires that Covered Entities report to CISA (1) any Covered Cyber Incident within 72 hours, and (2) any Ransomware Attack that results in a ransom payment within 24 hours. CIRCIA also requires Covered Entities to promptly submit certain supplemental reports providing updated or additional information about the incident following the initial submission. While CIRCIA included specific definitions for Ransomware Attack and Ransom Payment, which the Proposed Rule largely aligns with, CIRCIA directed CISA to provide a definition with more detailed criteria for a Covered Cyber Incident as part of the rulemaking process.
The Proposed Rule would define a Covered Cyber Incident to include two subsidiary definitions – a Cyber Incident and a Substantial Cyber Incident. First, the Proposed Rule provides a definition for the term Cyber Incident—that is, an occurrence that actually jeopardizes, without lawful authority, the integrity, confidentiality, or availability of information on an information system, or actually jeopardizes, without lawful authority, an information system. A Cyber Incident that then meets certain impact-based criteria would be considered a Substantial Cyber Incident. Finally, a Covered Cyber Incident would be defined as any Substantial Cyber Incident experienced by a Covered Entity.
The Proposed Rule states that a Cyber Incident must meet certain impact-based criteria in order to be a Substantial Cyber Incident. There are four such criteria and an incident needs to meet only one of the four criteria to constitute a Substantial Cyber Incident.
- Substantial Loss of Confidentiality, Integrity, or Availability. The first criterion is a “substantial” loss of confidentiality, integrity, or availability (“CIA”) of an information system (including operational technology, or OT) or a network. The Proposed Rule notes that whether loss is “substantial” will depend on a variety of factors, including the type, volume, impact, and duration of the loss, such as an attack that cuts off services for an extended period or persistent access to information systems by a threat actor.
- Serious Impact on Safety and Resilience. The second criterion is a “serious” impact on the safety and resiliency of operational systems and processes. The Proposed Rule cites to NIST definitions of safety and resilience, and notes that “serious” will also depend on a variety of factors, such as the safety hazards posed by an incident. For example, the Proposed Rule states that cyber incidents that noticeably increases the potential for a release of hazardous chemicals used in chemical manufacturing or water purification, disrupts or compromises a BES cyber system that performs reliability tasks in the electric grid, or disrupts the ability of a communications service provider to transmit or deliver 911 calls would meet this definition.
- Significant Operational Disruption. The third is a disruption of the ability to engage in business or industrial operations, or deliver goods or services, due to: (1) an attack (including, but not limited to a denial-of-service attack, ransomware attack, or exploitation of a zero-day vulnerability) against (i) an information system or network or (ii) an operational technology system or process; or (2) a loss of service facilitated through, or caused by, a compromise of a cloud service provider (“CSP”), managed service provider (“MSP”), other third-party data hosting provider, or by a supply chain compromise. The Proposed Rule’s commentary notes that the disruption must be significant, akin to the “substantial” and “serious” qualifiers discussed above.
- Significant Third-Party Compromise. The last criterion is unauthorized access to an information system or network, or any nonpublic information contained therein, that is facilitated through or caused by either a compromise of a CSP, MSP, other third-party data hosting provider, or a supply chain compromise. While similar to the loss of CIA, this criterion is focused on third-party and supply chain compromise. Again, the Proposed Rule’s commentary notes that the impacts must be significant to meet this criterion.
CISA states in the Proposed Rule that it interprets CIRCIA to limit the fourth criterion to unauthorized access that is achieved by the enumerated causes set forth in CIRCIA’s original statutory text (e.g., compromise of a CSP or supply chain compromise). To avoid ambiguity, the Proposed Rule includes a statement that a Cyber Incident that impacts a Covered Entity and results in any of the impacts identified in the first three criteria is a Substantial Cyber Incident, regardless of what caused the incident. In other words, the first three criteria are not limited by the source of a compromise (e.g., third-party compromise) or a particular attack vector (e.g., exploitation of a zero-day).
Exceptions
The Proposed Rule includes three exceptions to reporting requirements. First, Covered Entities are not required to report to CISA if the entity provides a legally required incident report to another federal agency that contains substantially similar information, is provided in a substantially similar timeframe, and can be shared within that timeframe under an information sharing agreement between CISA and the federal agency. Second, the Proposed Rule exempts critical infrastructure owned, operated, or governed by multi-stakeholder organizations that develop, implement, and enforce policies concerning the Domain Name System. Third, federal agencies required by the Federal Information Security Modernization Act to report incidents to CISA are exempt from reporting those incidents under CIRCIA.
Other Matters
The Proposed Rule addresses various other aspects of CIRCIA, including incident reporting content requirements and mechanisms, data and records preservation requirements, enforcement mechanisms, and additional definitions (e.g., CSP and Information System).
This post was originally published on the 3rd party site mentioned in the title of this this site