The newly released update in early 2024 of the NIST Cybersecurity Framework (CSF) from 1.1 to 2.0 represents a significant step forward in cybersecurity management and reflects the latest advancements in technology and threat mitigation. As organizations prepare for this transition, understanding the changes that will be required is critical for crafting an actionable transition
Insight #1 According to Google, zero days being exploited in the wild jumped 50% last year. I just don’t understand your thought process if you are not looking at control layers like Runtime Security to help detect and prevent these unknown vulnerabilities. *** This is a Security Bloggers Network syndicated blog from AppSec Observer authored
Building on our previous discussion about the pivotal role of Trusted Platform Modules (TPMs) in securing distributed ID and payment card printers, it’s important to delve deeper into strengthening security within distributed payment systems. There are many cutting-edge solutions and strategies that enhance security in distributed payment environments. Advancements in Software for Payment Card Printers
Computer scientists have uncovered a shockingly prevalent misconfiguration in popular enterprise cloud-based email spam filtering services, along with an exploit for taking advantage of it. The findings reveal that organizations are far more open to email-borne cyber threats than they know. In a paper that will be presented at the upcoming ACM Web 2024 conference
The editors at Solutions Review have curated this list of the most noteworthy identity management and information security news for the week of March 28. This curated list features identity management and information security vendors such as The U.S. State Department, SydeLabs, UiPath, and more. Keeping tabs on all the most relevant identity management and information
Several Russian companies have been subjected to intrusions exploiting the already-patched WinRAR vulnerability, tracked as CVE-2023-38831, by the PhantomCore cyberespionage operation, which has been linked to Ukraine, reports The Record, a news site by cybersecurity firm Recorded Future. Attacks commenced with the distribution of phishing emails with a contract-spoofing PDF document and a password-protected RAR
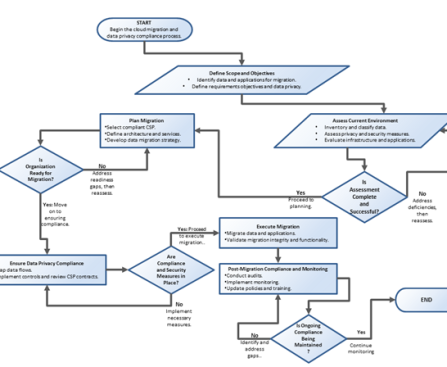
Over the past decade, enterprises have increasingly shifted their operations to the cloud for enhanced efficiency, scalability, and cost savings. Gartner predicts that by 2025, over 85% of organizations will embrace a cloud-first principle, and cloud spending will surpass 45% of all enterprise IT spending. When implementing cloud solutions, ensuring regulatory compliance and establishing a
Each business day MSSP Alert delivers a quick lineup of news, analysis, and chatter from across the MSSP, MSP, and cybersecurity world. Reaching Our Inbox: Send news, tips and rumors to Managing Editor Jim Masters: [email protected] Today’s MSSP Alert Market News: 1. Threat Intelligence Release: DarkLight, a cybersecurity solutions provider, has delivered new threat intelligence and enrichment
Photo by KeepCoding / Unsplash Rubrik, a cloud data management company backed by Microsoft, has made plans to file an IPO next week, according to Bloomberg sources. In 2021, Rubrik made a deal with Microsoft, which saw the tech giant make an equity investment and value the company at $4 billion. According to Bloomberg News,
Securing applications in these times of high-velocity digital transformation is an uphill battle. The challenges of developing secure applications within a DevOps pipeline continue to exist, and new issues arise when infrastructure and code are deployed automatically. With cloud migration on the rise, organizations are moving to a new phase of security practices. Infrastructure is now treated as code. This