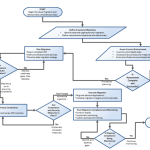
Several Russian companies have been subjected to intrusions exploiting the already-patched WinRAR vulnerability, tracked as CVE-2023-38831, by the PhantomCore cyberespionage operation, which has been linked to Ukraine, reports The Record, a news site by cybersecurity firm Recorded Future.
Attacks commenced with the distribution of phishing emails with a contract-spoofing PDF document and a password-protected RAR archive, which when executed delivers the PhantomRAT remote access malware that allows data exfiltration, a report from Russian Group-IB spinoff F.A.C.C.T revealed. While three PhantomRAT test samples were discovered to be from Ukraine, such an attribution could not be verified by most Western cybersecurity firms due to being cut off from Russian networks following the Russia-Ukraine war.
Check Point researchers confirmed the operational nature of PhantomRAT. However, attack activity linked to PhantomCore has not been identified by Microsoft, according to Microsoft Director of Threat Intelligence Strategy Sherrod DeGrippo, who also noted that the usage of RAR archives for malware delivery has already been found in previous attack campaigns.
This post was originally published on the 3rd party site mentioned in the title of this this site