How implementing a trust fabric strengthens identity and network
At Microsoft, we’re continually evolving our solutions for protecting identities and access to meet the ever-changing security demands our customers face. In a recent post, we introduced the concept of the trust fabric. It’s a real-time approach to securing access that is adaptive and comprehensive. In this blog post, we’ll explore how any organization—large or small—can chart its own path toward establishing their own digital trust fabric. We’ll share how customers can secure access for any trustworthy identity, signing in from anywhere, to any app or resource on-premises, and in any cloud. While every organization is at a different stage in their security journey, with different priorities, we’ll break down the trust fabric journey into distinct maturity stages and provide guidance to help customers prioritize their own identity and network access improvements.
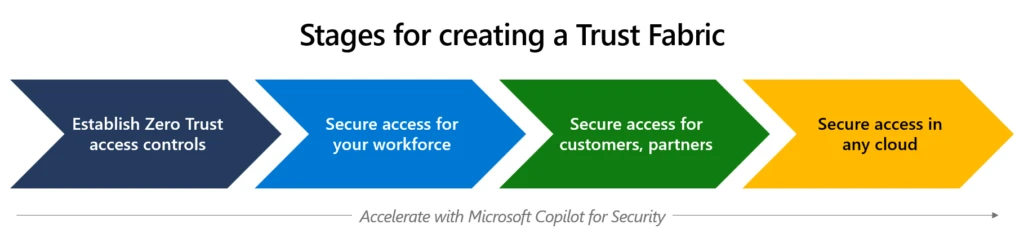
Stage 1: Establish Zero Trust access controls
“Microsoft enabled secure access to data from any device and from any location. The Zero Trust model has been pivotal to achieve the desired configuration for users, and Conditional Access has helped enable it.”
—Arshaad Smile, Head of Cloud Security, Standard Bank of South Africa
This first stage is all about your core identity and access management solutions and practices. It’s about securing identities, preventing external attacks, and verifying explicitly with strong authentication and authorization controls. Today, identity is the first line of defense and the most attacked surface area. In 2022, Microsoft tracked 1,287 password attacks every second. In 2023 we saw a dramatic increase, with an average of more than 4,000 password attacks per second.1
To prevent identity attacks, Microsoft recommends a Zero Trust security strategy, grounded in the following three principles—verify explicitly, ensure least-privilege access, and assume breach. Most organizations start with identity as the foundational pillar of their Zero Trust strategies, establishing essential defenses and granular access policies. Those essential identity defenses include:
- Single sign-on for all applications to unify access policies and controls.
- Phishing-resistant multifactor authentication or passwordless authentication to verify every identity and access request.
- Granular Conditional Access policies to check user context and enforce appropriate controls before granting access.
In fact, Conditional Access is the core component of an effective Zero Trust strategy. Serving as a unified Zero Trust access policy engine, it reasons over all available user context signals like device health or risk, and decides whether to grant access, require multifactor authentication, monitor or block access.
Recommended resources—Stage 1
For organizations in this stage of their journey, we’re detailing a few recommendations to make it easier to adopt and advance Zero Trust security fundamentals:
- Implement phishing-resistant multifactor authentication for your organization to protect identities from compromise.
- Deploy the recommended Conditional Access policies, customize Microsoft-managed policies, and add your own. Test in report-only mode. Mandate strong, phishing-resistant authentication for any scenario.
- Check your Microsoft Entra recommendations and Identity Secure Score to measure your organization’s identity security posture and plan your next steps.
Stage 2: Secure access for your hybrid workforce
Once your organization has established foundational defenses, the next priority is expanding Zero Trust strategy by securing access for your hybrid workforce. Flexible work models are now mainstream, and they pose new security challenges as boundaries between corporate networks and open internet are blurred. At the same time, many organizations increasingly have a mix of modern cloud applications and legacy on-premises resources, leading to inconsistent user experiences and security controls.
The key concept for this stage is Zero Trust user access. It’s about advanced protection that extends Zero Trust principles to any resource, while making it possible to securely access any application or service from anywhere. At the second stage of the trust fabric journey, organizations need to:
- Unify Conditional Access across identity, endpoint, and network, and extend it to on-premises apps and internet traffic so that every access point is equally protected.
- Enforce least-privilege access to any app or resource—including AI—so that only the right users can access the right resources at the right time.
- Minimize dependency on the legacy on-premises security tools like traditional VPNs, firewalls, or governance that don’t scale to the demands of cloud-first environments and lack protections for sophisticated cyberattacks.
A great outcome of those strategies is much improved user experience, as now any application can be made available from anywhere, with familiar, consistent sign-in experience.
Recommended resources—Stage 2
Here are key recommendations to secure access for your employees:
- Converge identity and network access controls and extend Zero Trust access controls to on-premises resources and the open internet.
- Automate lifecycle workflows to simplify access reviews and ensure least privilege access.
- Replace legacy solutions such as basic Secure Web Gateway (SWG), Firewalls, and Legacy VPNs.
Stage 3: Secure access for customers and partners
With Zero Trust user access in place, organizations need to also secure access for external users including customers, partners, business guests, and more. Modern customer identity and access management (CIAM) solutions can help create user-centric experiences that make it easier to securely engage with customers and collaborate with anyone outside organizational boundaries—ultimately driving positive business outcomes.
In this third stage of the journey towards an identity trust fabric, it’s essential to:
- Protect external identities with granular Conditional Access policies, fraud protection, and identity verification to make sure security teams know who those external users are.
- Govern external identities and their access to ensure that they only access resources that they need, and don’t keep access when it’s no longer needed.
- Create user-centric, frictionless experiences to make it easier for external users to follow your security policies.
- Simplify developer experiences so that any new application has strong identity controls built-in from the start.
Recommended resources—Stage 3
- Learn how to extend your Zero Trust foundation to external identities. Protect your customers and partners against identity compromise.
- Set up your governance for external users. Implement strong access governance including lifecycle workflows for partners, contractors, and other external users.
- Protect customer-facing apps. Customize and control how customers sign up and sign in when using your applications.
Stage 4: Secure access to resources in any cloud
The journey towards an organization’s trust fabric is not complete without securing access to resources in multicloud environments. Cloud-native services depend on their ability to access other digital workloads, which means billions of applications and services connect to each other every second. Already workload identities exceed human identities by 10 to 1 and the number of workload identities will only grow.2 Plus, 50% of total identities are super identities, that have access to all permissions and all resources, and 70% of those super identities are workload identities.3
Managing access across clouds is complex, and challenges like fragmented role-based access control (RBAC) systems, limited scalability of on-premises Privileged Access Management (PAM) solutions, and compliance breaches are common. These issues are exacerbated by the growing adoption of cloud services from multiple providers. Organizations typically use seven to eight different products to address these challenges. But many still struggle to attain complete visibility into their cloud access.

We’re envisioning the future for cloud access management as a unified platform that will deliver comprehensive visibility into permissions and risk for all identities—human and workloads—and will secure access to any resources in any cloud. In the meantime, we recommend the following key actions for in the fourth stage of their journey towards the trust fabric:
Read our recent blog titled “Securing access to any resource, anywhere” to learn more about our vision for Cloud Access Management.
Recommended resources—Stage 4
As we work towards making this vision a reality, customers today can get started on their stage four trust fabric journey by learning more about multicloud risk, getting visibility, and remediating over-provisioned permissions across clouds. Check out the following resources to learn more.
- Understand multicloud security risks from the 2024 State of Multicloud Security Risk Report.
- Get visibility into cloud permissions assigned to all identities and permissions assigned and used across multiple clouds and remediate risky permissions.
- Protect workload-to-workload interactions by securing workload identities and their access to cloud resources.
Accelerate your trust fabric with Generative AI capabilities and skills
To increase efficiency, speed, and scale, many organizations are looking to AI to help augment existing security workflows. Microsoft Entra and Microsoft Copilot for Security work together at machine speed, integrating with an admin’s daily workflow to prioritize and automate, understand cyberthreats in real time, and process large volumes of data.
Copilot skills and capabilities embedded in Microsoft Entra helps admins to:
- Discover high risk users, overprivileged access, and suspicious sign-ins.
- Investigate identity risks and help troubleshoot daily identity tasks.
- Get instant risk summaries, steps to remediate, and recommended guidance for each identity at risk.
- Create lifecycle workflows to streamline the process of provisioning user access and eliminating configuration gaps.
Copilot is informed by large-scale data and threat intelligence, including the more than 78 trillion security signals processed by Microsoft each day, and coupled with large language models to deliver tailored insights and guide next steps. Learn more about how Microsoft Copilot for Security can help support your trust fabric maturity journey.
Microsoft Entra
Protect any identity and secure access to any resource with a family of multicloud identity and network access solutions.

Microsoft is here to help
No matter where you are on your trust fabric journey, Microsoft can help you with the experience, resources, and expertise at every stage. The Microsoft Entra family of identity and network access solutions can help you create a trust fabric for securing access for any identity, from anywhere, to any app or resource across on-premises and clouds. The products listed below work together to prevent identity attacks, enforce least privilege access, unify access controls, and improve the experience for users, admins, and developers.

Learn more about securing access across identity, endpoint, and network to accelerate your organization’s trust fabric implementation on our new identity and network access solution page.
Learn more
To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us on LinkedIn (Microsoft Security) and X (@MSFTSecurity) for the latest news and updates on cybersecurity.
1Microsoft Digital Defense Report 2023.
2How do cloud permission risks impact your organization?, Microsoft.
32024 State of Multicloud Security Risk Report, Microsoft.
This post was originally published on the 3rd party site mentioned in the title of this this site