When a company intends to acquire another organization through a merger or purchase, it is important to know what security risks could accompany the acquisition. Without this, organizations could open themselves to significant financial and legal challenges.
Following an M&A, IT teams must merge different technologies and resources as the participating organizations become increasingly interconnected. A newly acquired environment brings its own IT systems, networks, and user accounts – along with its own unique risks – to an existing infrastructure. This can result in a highly complex environment where administrators may struggle to understand all the consolidated entity’s resources, applications, and users.
The new consolidated entity needs to be able to combine all domains and resources to a single unified IT infrastructure. This means understanding the type of accounts and resources you need to migrate; for example, which accounts are service accounts and what kind of applications you need to merge. In most cases, the IT team won’t know much about the acquired environment or its users.
This lack of visibility across the new environment, its resources and its users creates a major blind spot – and potentially many more security risks.
Silverfort’s Domain Consolidation Protection
With Silverfort, organizations can quickly and easily migrate the new environment’s resources and users to the main entity domain, accelerating the post-merger integration process. Silverfort can also offer organizations complete visibility of their existing and incoming environments, allowing them to protect both and pinpoint any risks associated with the integration. By enforcing new security measures with Silverfort, organizations can proactively defend against incoming cyber threats such as lateral movement attacks.
.ai-rotate {position: relative;}
.ai-rotate-hidden {visibility: hidden;}
.ai-rotate-hidden-2 {position: absolute; top: 0; left: 0; width: 100%; height: 100%;}
.ai-list-data, .ai-ip-data, .ai-filter-check, .ai-fallback, .ai-list-block, .ai-list-block-ip, .ai-list-block-filter {visibility: hidden; position: absolute; width: 50%; height: 1px; top: -1000px; z-index: -9999; margin: 0px!important;}
.ai-list-data, .ai-ip-data, .ai-filter-check, .ai-fallback {min-width: 1px;}
Visibility and Monitoring of Service Accounts
Silverfort automatically identifies all service accounts and monitors their authentication and behavior within a consolidated environment. Silverfort is able to accomplish this as machine and service accounts exhibit predictable behavior patterns, allowing for automatic identification and categorization on the Service Accounts screen.
Silverfort also supports Group Managed Service Accounts (gMSA) and offers a filter that allows you to see every gMSA in your system. Each gMSA will be detected and treated as any service account.
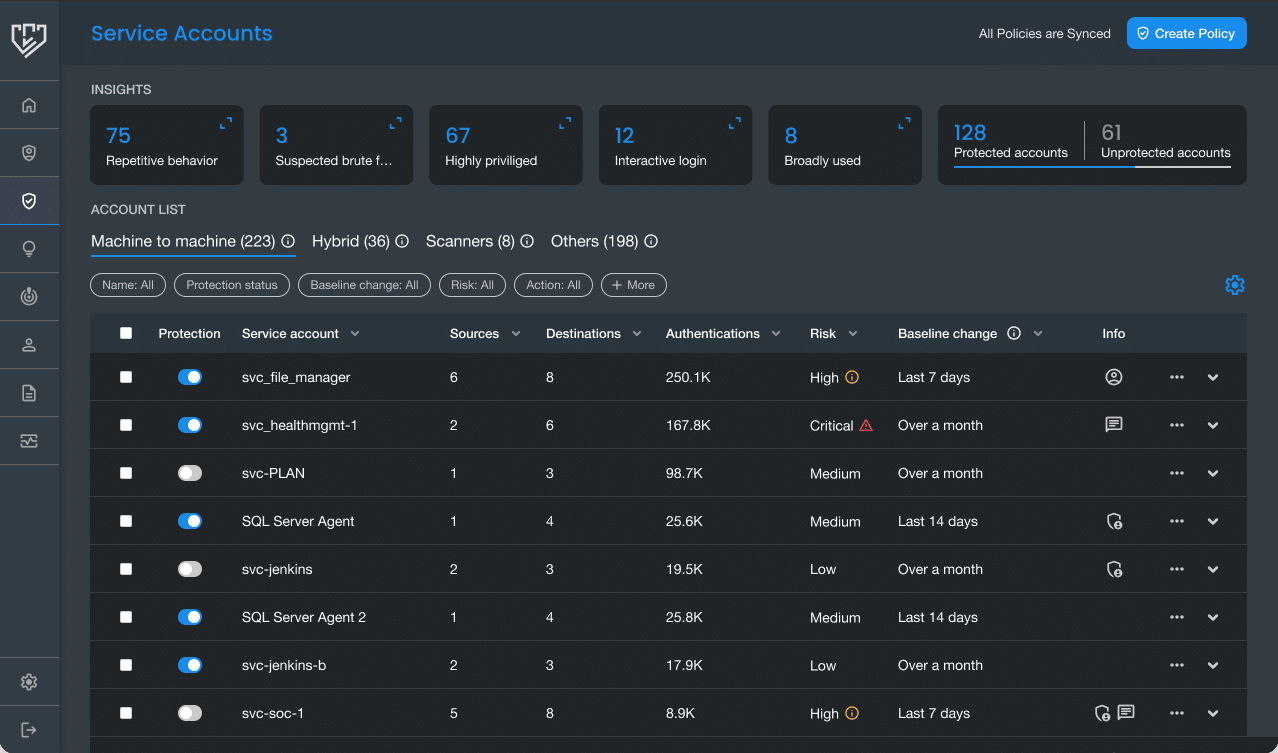
Silverfort identifies service accounts in several different ways:
• Behavioral Analysis – Silverfort tracks the account’s behavior to identify repetitive traffic patterns.
• AD Configuration – Silverfort checks the account’s attributes in AD to find characteristics common to service accounts.
• Naming Conventions – Silverfort holds a repository of naming conventions typically used for service accounts.
• Custom Insights – Silverfort receives feedback from the admin regarding the structure of service accounts in the customer environments (like OU, SG, and naming conventions).
• gMSA – The different account types defined in AD are used as service accounts.
Monitoring & Risk Analysis of Service Accounts
After all the migrated service accounts have been identified, you can monitor their activity and associated risks. Silverfort provides real-time insights and visibility into all service account details and behavior, while continuously monitoring and auditing their use.
With continuous monitoring of all authentication and access activities of all migrated service accounts, Silverfort can assess the risk associated with every authentication attempt and detect any suspicious behavior or anomalies.
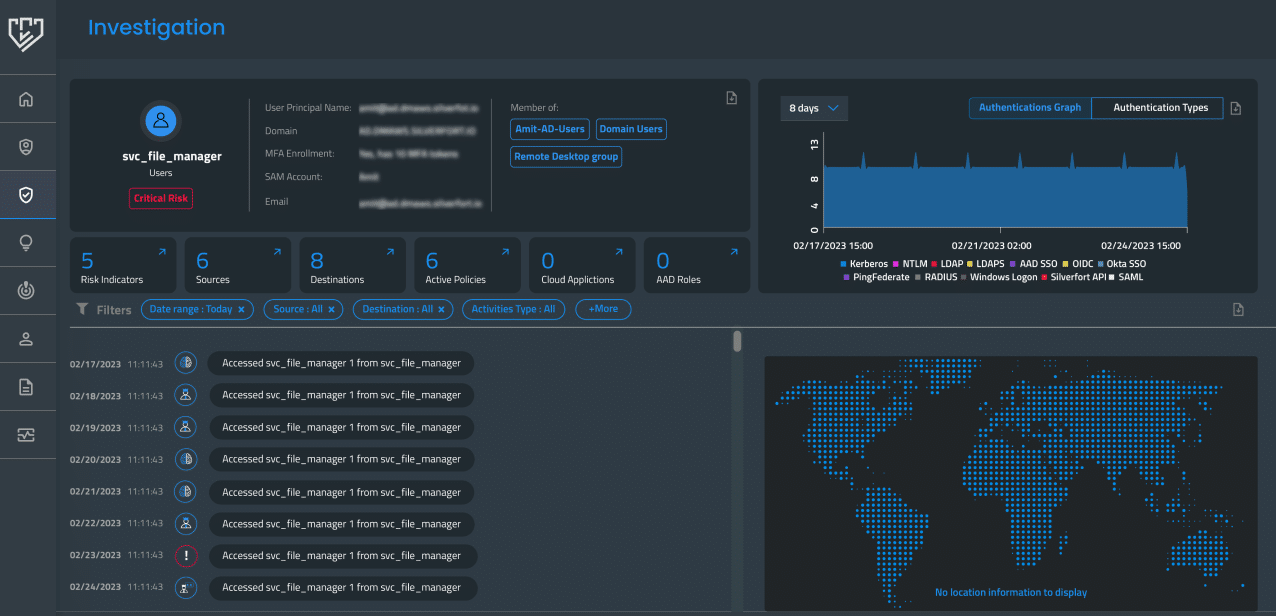
Visibility of User Activity & Authentications
Using the Logs screen in the Silverfort console, organizations will have complete visibility into all user logs and authentication activity. For those undergoing a merger, organizations will gain a better understanding of the incoming users, what they are trying to access, and what their risk score is.
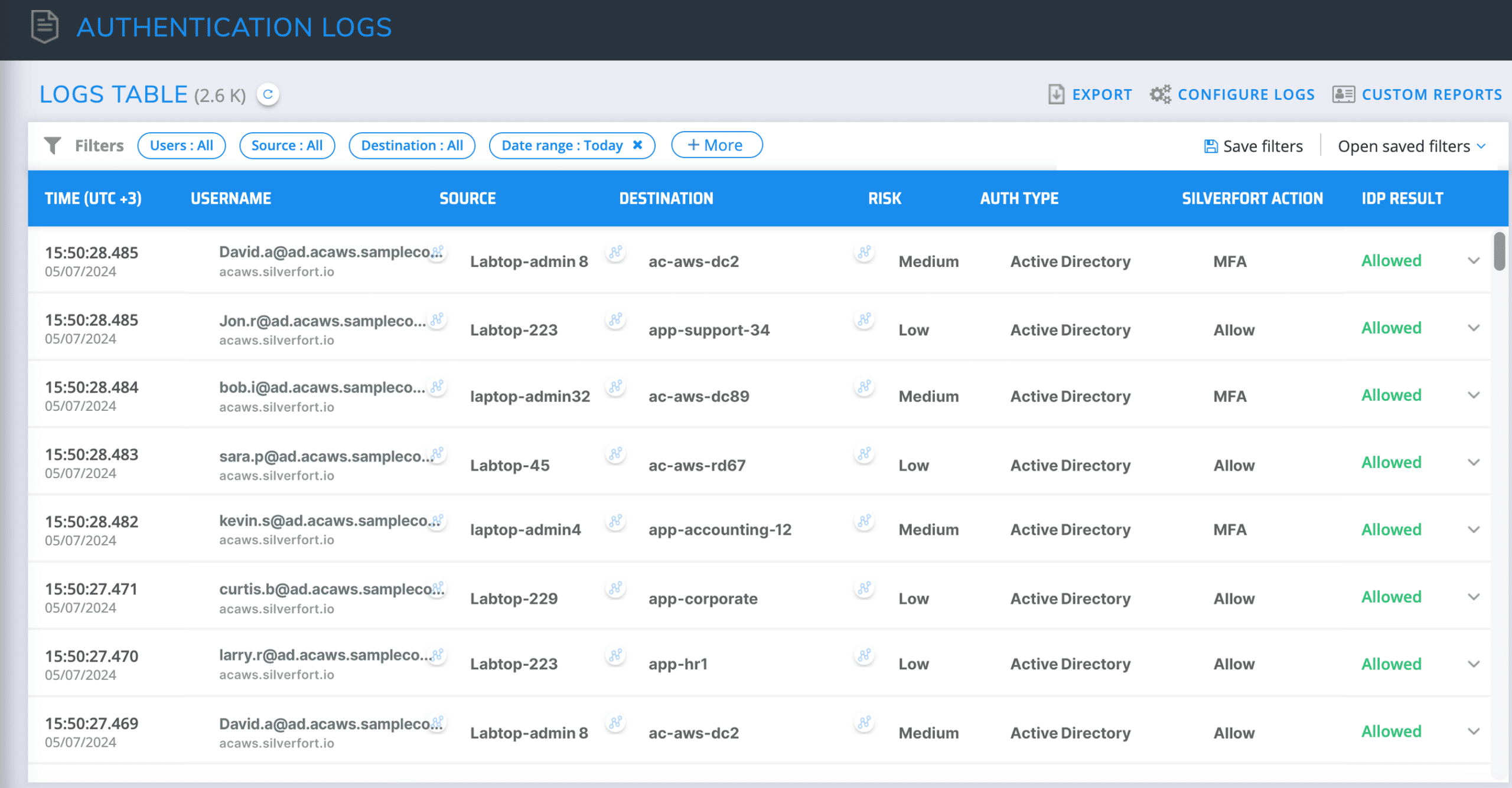
You can view details of a user’s logs, authentication activity and risk indicators, and gain more actionable insights by clicking the “investigate” icon next to the user in the Logs screen. With these details, organizations are equipped with complete visibility into each user and their authentication activity.
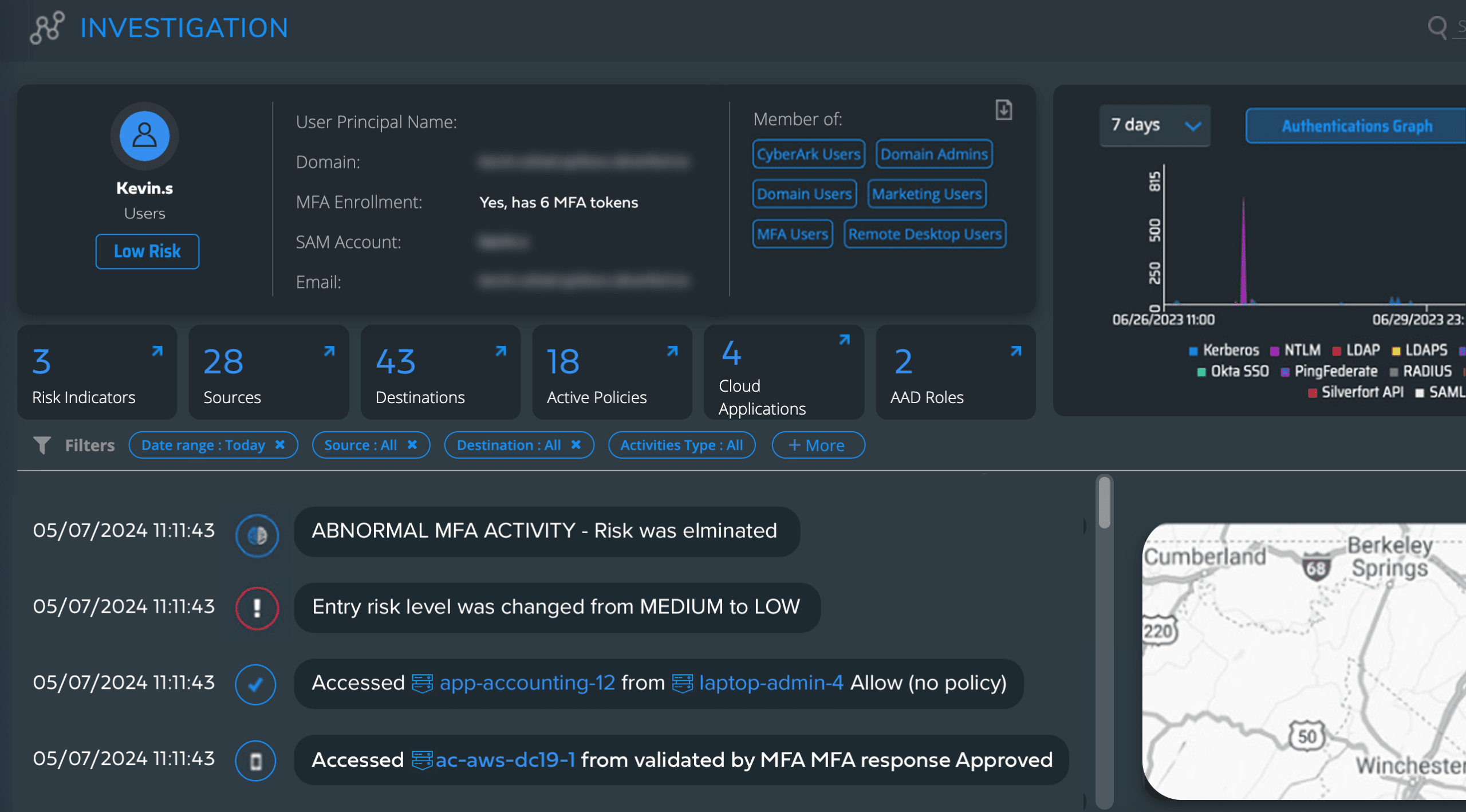
As a result of having full visibility into migrated resources, service accounts, and users, organizations can rest assured that their consolidated environment is being protected and their overall identity security posture management is up to date.
Authentication Firewall in Action: Preventing a Lateral Movement Attack Across Multi-Domains
The need for improved visibility and security controls across all domain entities during M&A was highlighted for one of Silverfort’s customers. During April 2024, a European manufacturer sought out our Identity Security Services to help them with their threat-hunting capabilities, as they understood one of the companies they had acquired had been compromised and subjected to a cyber attack.
As part of a larger acquisition, this customer had also acquired a smaller US-based entity which they integrated into their organization. At the time, they created a two-way trust between their entities’ domains to integrate the smaller domain into the newly consolidated organization. Unknown to the IT team, the acquired entity had limited security controls in place: they did not have any MFA protection for VPN access or any EDR on the endpoint. As a result, the acquired entity was compromised by malicious actors who attempted to move laterally from the smaller entity to the customer’s domain to conduct a ransomware attack.
The Attack Flow:
- Initial access: Using a secure VPN authentication, the attacker targeted three different users on seven servers with a brute force attack and successfully compromised them.
- Credential compromise: From its initial foothold in the environment and compromise of the target user, the attacker changed their password and created new users with the same privileges.
- Lateral movement: With the compromised account, the attacker attempted to move laterally to the larger domain, which is a Silverfort customer. The larger domain started to see malicious access attempts to their domain and reached out to Silverfort for assistance.
The Protection Flow:
- In Silverfort’s console and working with the Silverfort threat-hunting team, they understood they were being attacked and quickly applied deny access policies to stop any access from the compromised entity’s IP address.
- The customer’s security team segmented the entity’s domain to ensure no malicious access could occur in their domain. This immediately blocked the lateral movement.
- Following the implementation of an authentication firewall with deny policies and identity segmentation, the team used Silverfort to track the authentication trail of the compromised accounts to the patient zero machine. They were then able to conclude remediation and remove the remaining malicious presence from the compromised domain.
This example proves how vital it is to have an identity protection solution that offers authentication firewall capabilities, including deny access enforcement policies, and identity segmentation features. As a result of having real-time visibility and proactive security controls in place, the organization prevented an attack by threat actors who possessed compromised credentials.
Looking to gain complete visibility across your environment? Reach out to one of our experts here.
The post Identity Security in M&A: Gain Visibility into Consolidated Environments with Silverfort appeared first on Silverfort.
*** This is a Security Bloggers Network syndicated blog from Silverfort Blog – Cyber Security News authored by Zev Brodsky. Read the original post at: https://www.silverfort.com/blog/identity-security-in-ma-gain-visibility-with-silverfort/
This post was originally published on the 3rd party site mentioned in the title of this this site