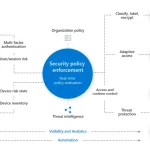
An increasing proportion of critical business infrastructure today exists in the cloud. Companies are investing more and more in digital assets and tools every day. In some industries, workflows are entirely cloud based, leaving a company’s lifeblood in the hands of digital infrastructure.
This trend hasn’t gone unnoticed by cybercriminals. They’ve taken to assaulting cloud infrastructure and databases to steal valuable information and hold businesses for ransom.
Cybersecurity is a burgeoning industry that seeks to combat would-be attackers. And cloud-native security takes the fight to the cloud.
This article will help you come to grips with cybersecurity for the cloud. Plus, we’ll dive into the critical benefits for your company.
.ai-rotate {position: relative;}
.ai-rotate-hidden {visibility: hidden;}
.ai-rotate-hidden-2 {position: absolute; top: 0; left: 0; width: 100%; height: 100%;}
.ai-list-data, .ai-ip-data, .ai-filter-check, .ai-fallback, .ai-list-block, .ai-list-block-ip, .ai-list-block-filter {visibility: hidden; position: absolute; width: 50%; height: 1px; top: -1000px; z-index: -9999; margin: 0px!important;}
.ai-list-data, .ai-ip-data, .ai-filter-check, .ai-fallback {min-width: 1px;}
What Is Cloud-Native Security?
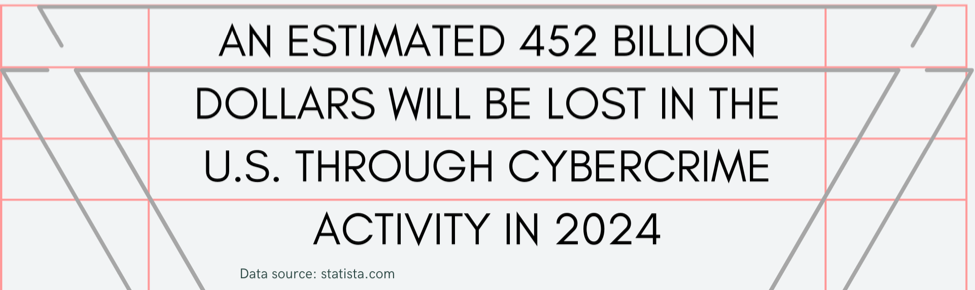
Cloud-native security is an all-encompassing solution that protects cloud-based infrastructure. That includes applications, databases, and CI/CD (continuous integration and continuous deployment) infrastructure. It’s the primary line of defense against the tirade of material cyberattacks, where will be lost in 2024.
Original image created by author
A robust package will integrate preventative and reactive security solutions to provide the best possible security, which a team of security experts maintains.
The critical aspects of a cloud-native security solution include:
- Secure storage of data and applications
- Powerful tools to manage access to resources
- The ability to monitor changing situations and assess threats
When Does a Business Need to Invest?
Fundamentally, all businesses should have some form of security in place. However, any company that relies on several cloud-based applications or storage containers to support operations must invest in a cloud-native security package.
Without proper safeguards, a successful attack could shut your business down overnight. It could also result in the loss of assets, whether you operate cloud-based contact center call routing solutions or a B2C ecommerce brand.
Assess your company’s current and aspirational infrastructure and measure it against the security measures in place.
- Have you been a victim of any threats or intrusion attempts so far?
- If so, was the security sufficient to repel it?
- How much of your infrastructure is cloud based?
- Will any new applications or expanding storage containers be vulnerable with the current security platform?
These sorts of questions can help you identify where changes to your system are required, and a move to a cloud-native security solution could be the best decision for your business.
In the UK, and 69% of large businesses suffered a breach of some kind during 2023. It goes to show how prevalent the issue has become, so it’s wise to take action.

Original image created by author
The 4 Cs of Cloud-Native Security
Successful cloud-native security implementations rely on the ‘four C’s’: cloud, cluster, container, and code. Each of these aspects represents a security layer that focuses on a different threat or demand. Together, they form the overall protection offered to cloud-based assets.
1. Cloud
This is the outer layer where everything is hosted and maintained. As this is the widest-reaching element of a cloud-native security environment, vulnerabilities are expansive so you need to carefully maintain them.
2. Cluster
Workloads that typically use the Kubernetes API – a common open-source platform to containerize workloads and services – will operate on this layer. At this stage, you’ll be engaging with applications and traffic on a regular basis.
Strong cross-cluster network protocols are a key part of effective defense to manage traffic and application activity. Ensure good credential hygiene for any accessing traffic to clusters. On top of this, use monitoring tools to regularly audit traffic and cluster activity.
3. Container
Applications and other resources are deployed within a containerized image and operated from this layer. Security concerns include vulnerabilities with the container or application itself as well as activity and traffic at this layer.
4. Code
The final layer of cloud-native security is the very code the infrastructure is built on. The security concerns lie within the written code. These often come from the use of third-party libraries or solutions that haven’t been effectively reviewed.
Ensure your developers use auditing tools to routinely review code to avoid vulnerabilities. In addition, avoid the use of third-party solutions without proper dependencies.

Free to use image sourced from Unsplash
Benefits of Cloud-Native Security for Businesses
Moving to a cloud-native security solution comes with a host of benefits for businesses of all sizes.
Here are several of the most readily apparent benefits, though the list extends beyond those discussed here.
We recommend that any medium to large-sized business invest in enterprise security solutions before an inevitable attack happens.
Automation at the Heart of Security
The real power of a cloud-based security solution comes through the levels of automation available. Businesses can benefit from deep insights into their network and application activity through automated monitoring and auditing tools. You can actively hunt for and highlight vulnerabilities, then the development team can better prepare for patching.
As with all forms of automation, maintain oversight at all times to get the best performance. Routinely explore insights and question them to see where improvements could be made or where anomalies arise.
Threat Deterrence
More often than not, the simple presence of a security system is enough to ward off potential attackers. The more robust your cloud-native security implementation is, the less likely it is that cybercriminals will try and penetrate it.
At the very least, their job will be harder. And there’s a better chance they’ll be caught, making it an unviable proposition.
It’s a fact that often goes unnoticed. So many businesses think their security isn’t being used effectively or has been overdesigned. As a result, they might reduce their investment in security to save financially. But, in fact, the opposite reality is true, so keep this in mind at all times. A security solution that doesn’t have to ‘work hard’ – i.e. repel consistent attacks – is a robust one.
Proactive Protection
Cloud-native security makes heavy use of analytics and auditing tools. These help to constantly monitor and understand the landscape of all managed cloud infrastructure, particularly when supported by smart encryption tools and in-depth access management.
Traditional security tends to favor a reactive approach. But this relies on impending threats to take any measures against it, often leading to breaches and exploitation of vulnerabilities.

Image created by author using Canva
Challenges of Cloud-Native Security
The use of cloud-native security is a must in 2024. Why? Because it’s effective as a safeguard from popular attack vectors, such as ransomware threats.
That said, it doesn’t come without distinct challenges that you need to understand and manage effectively.
Requires the Right Expertise to Integrate and Manage
The long-term maintenance of a cloud-native security environment demands a team of experts on hand. There’s simply no alternative.
Nearly every aspect of the environment, from the initial configuration to new application integration, requires a breadth of knowledge. And it may be that this expertise doesn’t exist in your company.
Make sure your business has a quality team to support your security efforts at all times. On top of this, regularly review the performance of your systems to avoid bandwidth issues.
Huge Range of Potential Threats to Combat
The list of potential cyber threats is extensive, bordering on limitless. And this problem is becoming more profound each and every day.
The latest development in cybercrime uses the power of artificial intelligence. This makes it capable of producing advanced deepfake malware attacks that trick individuals into providing sensitive financial or personal information to be used for nefarious purposes.
Security systems need to be regularly updated to ensure protection from the evolving list of threats.
Security Requirements Change Based on the Infrastructure
To complicate matters further, your business’ security needs are also defined by your infrastructure. Some businesses will only use cloud-based storage during typical operations. However, others might rely on workflow applications, cloud-based user account management and access, and even the very products themselves.
For example, the security needs of a self-contained data storage solution will be much simpler than a company supporting businesses wanting to know how to set up a virtual call center with cloud-based contact centers. In the latter example, in particular, the security concerns extend beyond the primary business in question too, as client data and infrastructure are now involved, complicating matters further.
Ensure you remain compliant with external partners you share security responsibilities with, and work to provide the necessary protection for complex infrastructures.

Image sourced free for use from Pexels
Next Steps
Cybercrime will affect nearly every business throughout their lifetime and you can never be sure when they’ll strike.
Cloud-based applications and services are a core aspect of modern business. But they also necessitate a robust security package to protect those valuable assets.
Review your current security situation and be honest with the quality of your protection. Where there are deficiencies, focusing on plugging holes and building a team that can grow your cloud-native security platform alongside your business.
The post Understanding Cloud-Native Security and Its Business Benefits appeared first on TuxCare.
*** This is a Security Bloggers Network syndicated blog from TuxCare authored by TuxCare Team. Read the original post at: https://tuxcare.com/blog/understanding-cloud-native-security-and-its-business-benefits/
This post was originally published on the 3rd party site mentioned in the title of this this site