It is expected that the yearly global cyber risk will surpass $10.5 trillion by 2025. Endpoints including workstations, servers, databases, laptops, and other devices have historically been the target of cyberattackers looking to steal sensitive data and systems for malicious purposes. However, a recent trend has shown that hackers are now concentrating on network infrastructure.
Switches, routers, firewalls, VPN appliances, DNS servers, and other network infrastructure devices that were formerly believed to be secure are increasingly open to attacks as new vulnerabilities are discovered, made public, and used against them. In this blog, we will understand about a recent incident which affected various router models.
Overview of the Incident
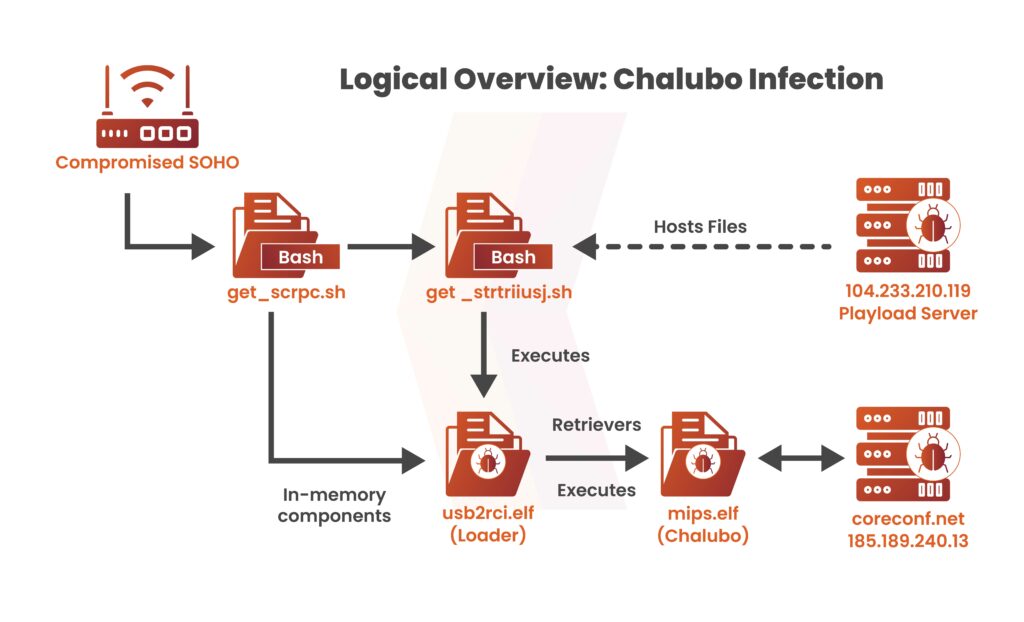
An unknown cyber attack targeted more than 600,000 small office/home workplace (SOHO) routers, rendering them inoperable, and disrupting customers’ internet and other computing resources. The attack affected three sorts of routers mainly: ActionTec3200, ActionTec T3260, and Sagemcom. Attackers used Chalubo, a remotely operated Trojan, to increase the chaos. The 72-hour incident exposed the vulnerability of SOHO routers and their susceptibility to cyber threats. Users had been left suffering with backlogs, experiencing huge downtime and damaged connections.
The scale and duration of the attack highlighted the need for strong cybersecurity measures to protect vital infrastructure and save organizations from such incidents in the future. Router reconfiguration efforts and their mitigation confronted major challenges, highlighting the effect of the attack and the importance of proactive safety features and vigilance towards evolving cyber threats.
The widespread nature of the attacks and the critical network equipment targeted highlighted the critical role routers play in maintaining internet connectivity. The attacks devastated many areas, demonstrating the connectedness of our digital world and how cyberattacks can impact global networks. Despite efforts to identify the attackers, their identities remain unknown, raising concerns about the motives and future attacks.
.ai-rotate {position: relative;}
.ai-rotate-hidden {visibility: hidden;}
.ai-rotate-hidden-2 {position: absolute; top: 0; left: 0; width: 100%; height: 100%;}
.ai-list-data, .ai-ip-data, .ai-filter-check, .ai-fallback, .ai-list-block, .ai-list-block-ip, .ai-list-block-filter {visibility: hidden; position: absolute; width: 50%; height: 1px; top: -1000px; z-index: -9999; margin: 0px!important;}
.ai-list-data, .ai-ip-data, .ai-filter-check, .ai-fallback {min-width: 1px;}
Impact of Network Infrastructure Attack on Organizations
Web attacks are unauthorized activities that target the digital assets of an organizational network infrastructure with the intent to destroy or steal personal data. The goal of the bad side is to infiltrate internal systems.
For example, an organization managing 1,000 requests per minute may be overwhelmed by 10,000 or more requests per minute, causing significant resource degradation and slow server and database performance. Such an attack would most likely affect the following areas in the following ways.
Data Corruption
A high volume of requests or unauthorized access can corrupt critical data for both the organization and its customers. This can disrupt order statuses and workflows, delay customer payments, and lead to ledger and financial data corruption. It causes significant issues during audits. Therefore, organizations must have data backups in place.
Financial Loss to Organization
To regain the trust of customers and stakeholders, an organization may need to offer compensation and incentives. In severe cases, they might also need to engage third-party organizations to handle and mitigate the attack. Additionally, if resources are charged per request, this could further increase the organization’s problems. If an attack occurs during a peak season or sales period, the loss of potential orders represents another financial setback. Repairing the lost assets also incurs additional costs.
Data Stealing
Attackers often target customer personal data, such as addresses, phone numbers, emails, and payment information, which can be exploited for social engineering or other malicious activities. Organizations with access to cameras and contacts can pose even greater risks to their users if compromised.
Operational Disruption
To recover from the attack, the organization may choose to halt operations and activities until systems are restored, causing significant delays in operational workflows.
How Network Infrastructure Attacks Can Be Prevented?
Your business can prevent many common network failure symptoms by reducing manual tasks through automation and maintaining thorough records. Additional methods to avoid network infrastructure issues include:
Switch to Cloud Services
Switching to cloud services is essential for avoiding data loss during an outage. Your business’s physical location should not be the primary storage for critical documents. Instead, utilize a cloud server, which is more reliable, convenient, and accessible. Cloud solutions allow you to access your data in the organization.
Contact Us for Network Penetration Testing Services
Back up Servers
To stay ahead of network infrastructure problems, conducting regular server backups is crucial to prevent downtime and data loss. Follow the 3-2-1 rule for effective server backups:
- Three copies of your data
- Two backups on different storage media
- One copy stored offsite
Ensure you verify that your server can be recovered in a disaster recovery scenario. This involves frequent testing to ensure that backups are saved correctly and can be restored after a disaster.
Implement a Backup Network Connection
To reduce network downtime, consider implementing a backup network connection. While some businesses can function for a few hours without the internet, many rely on continuous access. A backup network connection is a smart investment in such cases. By using different network carriers and providers, a redundant connection ensures that if one network experiences issues, another can take over and maintain connectivity.
Audit the Systems for Potential Threats
Finding the source of an outage or downtime is the first thing to do when it occurs in your company. For instance, you need to figure out whether a blown fuse or carrier disruptions are to blame for an unexpected internet outage at your company. Knowing where the network problem originated will also help you save time and money. Think about both internal and external risks and take action to safeguard your company from them in order to prevent system outages.
Kratikal’s Approach to Prevent Such Attacks
Understanding the Scope
The client’s scope must be clearly defined before an application assessment can be conducted. At this point, open dialogue between the company and the client is recommended to build a secure platform upon which to conduct assessments.
Information Gathering
At this step, a variety of OSINT (Open Source Intelligence) tools are used and tactics to gather as much data as they can on the target. The gathered data will help us comprehend how the relationship functions, which will enable us to precisely assess the risk as the engagement develops.
Identifying and Inspect
At this point, we combine computerized resources and tools with various data collection methods to create more advanced data. Any potential attack vectors are carefully examined by our experts. In the following step, the acquired data from this stage will serve as the foundation for its application.
Attack and Penetration
This is the last step in the entire assessment procedure. This stage involves gathering all acquired data, analyzing it, and providing the client with a comprehensive breakdown of our results. The entire report may have a thorough examination of every risk, and the final record may even include a summary of all the advantages and disadvantages.
Reporting
This is the last step in the entire assessment procedure. This stage involves gathering all acquired data, analyzing it, and providing the client with a comprehensive breakdown of our results. The entire report may have a thorough examination of every risk, and the final record may even include a summary of all the advantages and disadvantages.
.interestedBtn {
width: 70% !important;
box-sizing: border-box !important;
display: inline-block !important;
padding: 11px !important;
border: 1px !important;
border-color: #ddd !important;
margin-top: 10px !important;
background-color: #ec6e1d !important;
background-image: none !important;
text-shadow: none !important;
color: #fff !important;
font-size: 14px !important;
line-height: 20px !important;
border-radius: 5px !important;
margin: 0 !important;
cursor: pointer !important;
}
.inputBox {
width: 70% !important;
box-sizing: border-box !important;
padding: 5px 10px !important;
display: inline-block !important;
border: 1px solid #ddd !important;
background-color: #fff !important;
color: #444 !important;
font-size: 13px !important;
line-height: 20px !important;
border-radius: 5px !important;
}
.formSec {
float: left !important;
width: 55% !important;
}
.mainBox {
max-width: 600px !important;
margin: 0 auto !important;
border: 2px solid #eb7c35 !important;
padding: 20px !important;
font-family: Arial, Helvetica, sans-serif !important;
}
.boxDiv {
display: flex !important;
}
.boxConsult {
float: left !important;
width: 45% !important;
}
.formSecTwo {
text-align: right !important;
width: 100% !important;
}
.formHeading {
font-family: Arial, Helvetica, sans-serif !important;
margin-top: 0px !important;
font-weight: 700 !important;
line-height: 25px !important;
padding: 0px 5px 5px 10px !important;
font-size: 18px !important;
margin-bottom: 70px !important;
}
.fieldHeading {
margin: 0 !important;
font-size: 13px !important;
text-align: left !important;
margin: 0px 39px 2px 93px !important;
font-weight: 500 !important;
}
.image {
max-width: 100% !important;
height: auto !important;
}
@media screen and (max-width: 768px) {
.boxDiv {
display: block !important;
padding: 15px !important;
border: 2px solid #eb7c35 !important;
}
.image{
width: 60% !important;
}
.fieldHeading {
text-align: left !important;
margin: unset !important;
}
.boxConsult {
width: unset !important;
float: none !important;
}
.mainBox {
border: unset !important;
}
.form{
padding: 20px !important;
}
.formSec {
float: unset !important;
width: 100% !important;
}
.formSecTwo {
text-align: center !important;
}
.inputBox {
width: 100% !important;
}
.formHeading {
margin-bottom: unset !important;
}
.interestedBtn{
width: 100% !important;
}
}
Book a Free Consultation with our Cyber Security Experts

Conclusion
The most recent incident involving over 600,000 SOHO routers, which rendered them useless and obstructed users’ internet access, emphasizes the critical need for robust cybersecurity safeguards. The significant attack on a critical networking device underscores the critical role routers play in maintaining internet access and underscores the need of proactive security.
Kratikal, CERT-In empanelled auditor provides businesses with a wide range of cybersecurity solutions & services. Trusted by over 650+ SMEs and Enterprises worldwide, Kratikal delivers robust cybersecurity solutions. We are one of the fastest-growing firms committed to safeguarding companies and organizations of different sectors, for instance, SaaS, Fintech, Healthtech, Govt., etc., against cyber risks.
Ref: https://thehackernews.com/2024/05/mysterious-cyber-attack-takes-down.html
FAQs
- What is a router attack?
A routing attack is an attempt by a malicious entity to exploit flaws in a network’s architecture, causing it to split into multiple isolated components.
- How are routers attacked?
When hackers identify a vulnerable router, they exploit it by installing malware that provides persistence, enables distributed denial of service (DDoS) attacks, conceals malicious traffic, and more.
The post 60,000+ Vulnerabilities Exposed by the U.S. Router Cyber Attack appeared first on Kratikal Blogs.
*** This is a Security Bloggers Network syndicated blog from Kratikal Blogs authored by Shikha Dhingra. Read the original post at: https://kratikal.com/blog/60000-vulnerabilities-exposed-by-the-us-router-cyber-attack/
This post was originally published on the 3rd party site mentioned in the title of this this site