You may also like: As the world continues to embrace big data, increased connectivity, and automation, the internet of things (IoT) sector is booming. According to Verified Market Research, the global IoT market is all set to hit a $1319.08 billion valuation by 2026. On top of that, IoT solutions have the potential to make
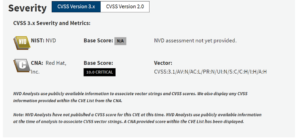
CVE-2024-3094 is a reported supply chain compromise of the xz libraries. The resulting interference with sshd authentication could enable an attacker to gain unauthorized access to the system. Overview Malicious code was identified within the xz upstream tarballs, beginning with version 5.6.0. This malicious code is introduced through a sophisticated obfuscation technique during the liblzma
IN a recent media briefing at AWS: Reinvent Security 2023 round-up, Phil Rodrigues, head of security at APJ Commercial, Amazon Web Services, presented how AWS ensures customer data remains secure from every type of threat. First off, Rodrigues said that AWS Security follows a Shared Responsibility Model where the AWS Cloud determines customer responsibility services
By Matt Schwager Trail of Bits is excited to introduce Ruzzy, a coverage-guided fuzzer for pure Ruby code and Ruby C extensions. Fuzzing helps find bugs in software that processes untrusted input. In pure Ruby, these bugs may result in unexpected exceptions that could lead to denial of service, and in Ruby C extensions, they
The newly released update in early 2024 of the NIST Cybersecurity Framework (CSF) from 1.1 to 2.0 represents a significant step forward in cybersecurity management and reflects the latest advancements in technology and threat mitigation. As organizations prepare for this transition, understanding the changes that will be required is critical for crafting an actionable transition
Insight #1 According to Google, zero days being exploited in the wild jumped 50% last year. I just don’t understand your thought process if you are not looking at control layers like Runtime Security to help detect and prevent these unknown vulnerabilities. *** This is a Security Bloggers Network syndicated blog from AppSec Observer authored
Building on our previous discussion about the pivotal role of Trusted Platform Modules (TPMs) in securing distributed ID and payment card printers, it’s important to delve deeper into strengthening security within distributed payment systems. There are many cutting-edge solutions and strategies that enhance security in distributed payment environments. Advancements in Software for Payment Card Printers
On March 27, 2024, the Cybersecurity & Infrastructure Security Agency (CISA) within the US Department of Homeland Security released a much-anticipated notice of proposed rulemaking (NPRM) to implement the Cyber Incident Reporting for Critical Infrastructure Act of 2022 (CIRCIA). Under the proposed rule, covered entities will have 72 hours to report to CISA a “covered
Listen to this post On March 27, 2024, the U.S. Cybersecurity and Infrastructure Agency (“CISA”) released an unpublished version of a Notice of Proposed Rulemaking (“NPRM”), as required by the Cyber Incident Reporting for Critical Infrastructure Act of 2022 (“CIRCIA”). The NPRM will be officially published on April 4, 2024, and comments are due by